Cybersecurity is an important topic that is constantly evolving. In this blog, Q2 Security Analyst Rebecca Tague tackles the subject of phishing kits. Check for more blogs from Rebecca throughout October as Q2 recognizes National Cybersecurity Awareness Month in the U.S.
Spam texts, fraudsters, and malicious websites are just a few ingredients of the recipe that has led to the proliferation of phishing kits/phishing-as-a-service attacks. Many sites that advertise phishing services to criminals are brought down by security/internet providers, authorities, or even both. However, these fraudulent sites can wreak personal and financial damage before being brought down. Unlike traditional fishing season, phishing season lasts all year—seven days a week, 24 hours a day.
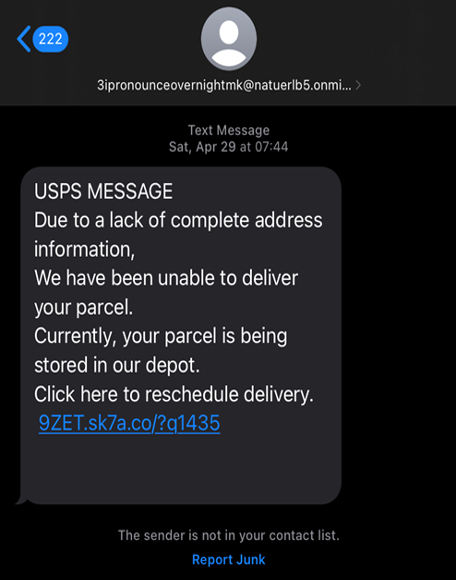
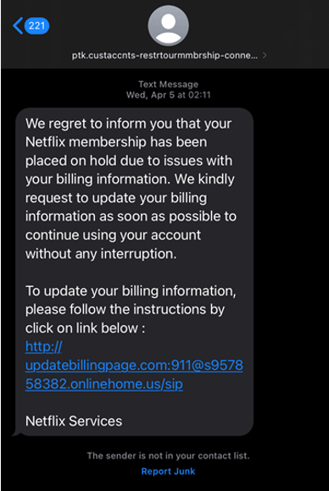
These phishing kits contain preconstructed code that enables fraudsters to build and maintain a phishing operation that is created by design to harvest personal data, financial data, and/or authentication methods. They operate by making initial contact with victims via text or email in the form of a fake alert/notification (see real-world examples below). The fraudulent message will typically include a link to a fake site hosted by the cybercriminal that, usually, is similar to the legitimate site. If the victim inputs their credentials or any other data, that information is harvested by the fraudster's API (application programming interface) and likely misused. Gmail and Telegram are popular channels that phishing websites leverage to handle stolen data collected by the phishing attempt. To further complicate matters, many phishing kits leverage multiple methods of handling the stolen data.
 |
 |
Phishing kits are becoming a more commonplace choice vector of fraud and data collection. According to ‘Group-IB,’ last year alone saw a 25% increase in the use of phishing kits, with 3,677 unique phishing kits, a 25% increase over 2021. As a technology develops, people will naturally fine tune it to their intentions; and with the growing popularity of these tools, there has been an increase in the number of evasion tactics fraudsters are employing that may pose an obstacle for conventional detection systems.
Where some phishing messages look entirely fake, some are more difficult to discern. Traditionally, fraudsters have employed tactics like spoofing (hiding a fake URL behind one that looks legitimate), however, as detection software has gotten more advanced, fraudsters have responded by advancing their techniques. By deploying evasion tactics like hypertext access, antibots, and directory randomization, they try to evade detection until they are able to extract their victims’ data. But not only are phishing kits extracting data from victims online, they are also extracting data from the criminals that utilize these kits. According to research from Imperva, about 25% of the phishing kits they analyzed forwarded phishing results and kit-buyer information to an additional recipient,most likely the creator of the kits. In these cases, fraudsters employing phishing kits may need to be ready to surrender their own data, as well as their victims’ data.
A successful phishing attack can have a heavy financial impact for companies and individuals alike. On the business scale, estimates suggest that the average successful phishing attack can reach up to $1.6 million, with reputation and legal fees at stake. For consumers, it can be an emotional headache to deal with changing all their accounts and needing to monitor their credit scores, not to mention any financial loss incurred.
But all hope is not lost. Within this past year alone, two major phishing-as-a-service groups were shut down: W3LL and 16shop. Both groups developed and sold tools to criminals to assist with carrying out cyberattacks, and both groups were subsequently shut down by authorities because of this. Although it is difficult for businesses and individuals to defend themselves completely from all threat vectors, there are many effective ways of mitigating the blast radius of phishing kits. These strategies include:
- Educate people that companies and services will most likely never reach out requesting sensitive information, like their social security number or login credentials. If ever in doubt about a message received, always reach out and verify the legitimacy of the message through a trusted channel, such as directly through the application or on a support line found on the legitimate website.
- Foster a community of security awareness for yourself and for the people around you by practicing healthy security posture.
- Make sure your passwords are globally unique and do not share a password via email, text, or phone with any unverifiable parties.
- Take note of any grammatical errors or any slight changes to a login or authentication page. Attackers will often try to copy the content delivery network (CDN) material of the site they are trying to collect data from in order to trick the user base, so the fraudulent site may look very similar to the legitimate one.
- Use certificate transparency logs and tools that monitor any CDN files being copied from your sites. Choose the right security solutions for you and/or your organization.
- If one of your accounts has been affected by a phishing attack, assume all associated accounts with similar information could be affected. If an account breach or suspected account breach ever occurs, update all credentials to prevent further attacks.
So, whatever you do, don't click the links when you receive a suspicious message!




