At Q2, we have the honor of protecting over 35 million end users moving over $3 trillion across our various products. It’s a job we take very seriously. We manage 41 petabytes of data (41,000,000,000,000,000) spread across our 12 distributed cloud hosting environments. Protecting all of this data would be simpler if we could just keep it tucked away under the layers and layers of our award-winning security posture – but unfortunately, we can’t.
Instead, we have to “poke holes” through it to allow customers and employees to engage with the applications – and engage they do, driving over 4.5 billion logins and another 12 billion API requests annually, equating to 32,000 inbound touches every minute, 24-7.
Separating the legitimate touch points from the bad actors trying to get in is the “art” -- and key to success in our protection layers. It’s a system with a proven track record. In 2020, Q2 blocked over 49 billion sessions from ever reaching the application layer, stopping over 93,000 bad sessions every minute of the day. To put things into perspective, that represents three times the number of good sessions.
Q2 operates a mature Distributed Cloud environment, combining the best of Private Cloud Active-Active Data Centers with a Multi-Cloud Public Cloud offering. We bring our own orchestration layer to these environments, allowing us to dynamically position the workloads where we want, and allowing us to move them later. All this, surrounded by a single security and compliance posture. The components are woven together into a seamless end-user experience.
Q2’s Distributed Cloud offers our customers a leap ahead in our innovation foundation, as more of the market’s ecosystem leans in to extend on Q2 services and leverage the Q2 Platform. The cybersecurity mesh allows us to accelerate our innovation because we are so secure.
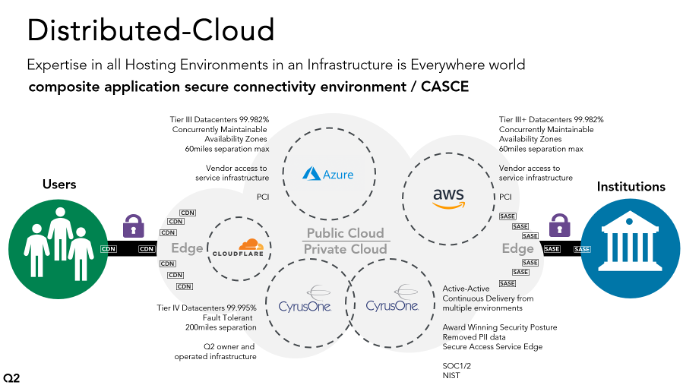
The challenge we face is that we simply can’t built a single moat around all this infrastructure:
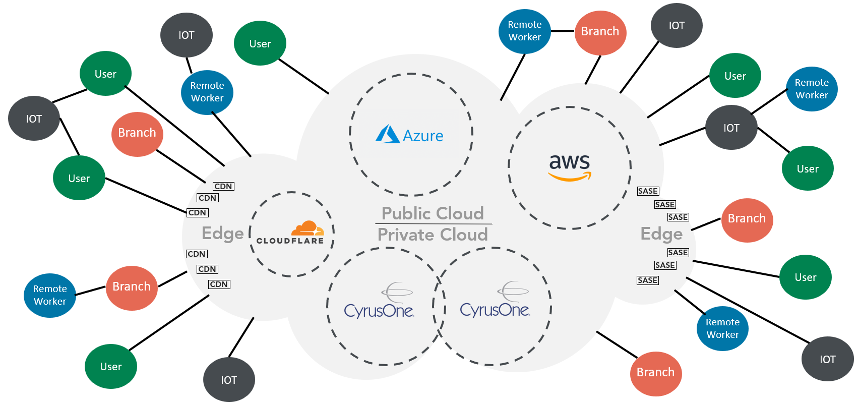
Traditionally, organizations protected their data using a perimeter approach: what was inside was trusted, what was outside was not. But now, the perimeter is much more fragmented - there is no longer an “inside” or “outside”. Data lives everywhere — people, applications, networks and devices are always moving and no longer operating within an organization’s geographic “fence”.
This scattered environment gave rise to the “trust no one” approach, which led to the implementation of Q2’s zero-trust security strategy in 2018.
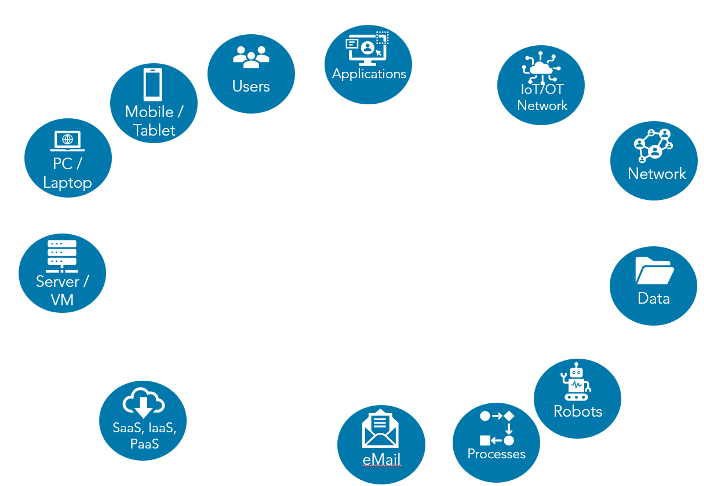
So, what’s the cybersecurity mesh and how did Q2 evolve to this growing technology trend?
It begins with the way many companies start building their security ecosystems. They buy point products to enhance their cybersecurity posture and fill specific gaps in their security strategy. These point products each tend to have a precise focus, such as data loss protection, intrusion detection, etc.
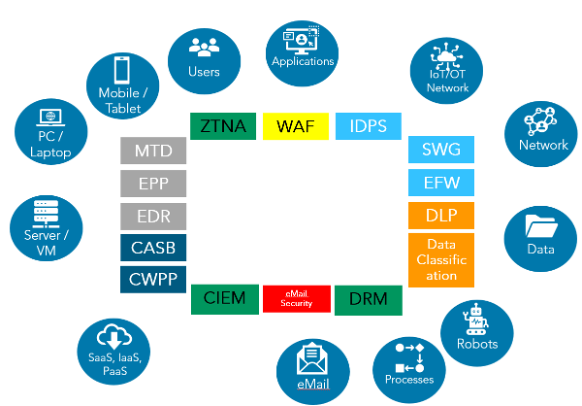
There are some specific integrations between different products, usually driven by vendors or sometimes by support for standards. Still, these products basically act independently, each “minding its own business” without sharing data with the others. A common pattern for integrating products is through security information and event management (SIEM) solutions, where a SIEM solution consumes events from these products. Security orchestration, analytics and reporting (SOAR) can configure responses based on the analysis of these events coming from all products.
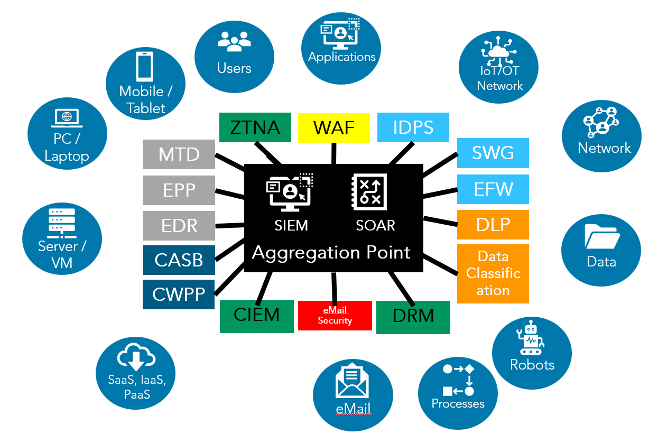
This process is what evolves into the cybersecurity mesh architecture (CSMA). It enables Q2 to build more connections between tools by having them indirectly (through the cybersecurity mesh) collaborate, learn from and influence each other. Security postures can work across different security products, so security intelligence becomes more effective and more predictive.
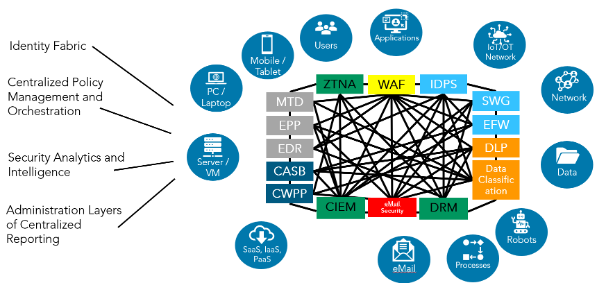
The “art” of the mesh is to utilize the best of each solution, in collaboration, to identify the good and the bad in an ever-expanding attack surface. We gain richer visibility into security events while reducing the complexity of operating each of these solutions independently. It could be compared to the simple genius of a hive.
The path a user session must take from the internet through the layers of our security mesh:

After all that, the session then navigates our physical load balancing, then our orchestration load balancers, then finally to the application layer, where all the many embedded application security features take over.
This is then all backed with the removal of sensitive data from the environment with Q2 Trustview™, our award-winning use of tokens, encoding and blockchain – which is being rolled out across our product line.
Each one of the layers individually inspects the session, informed by the other tools through a common analytics and intelligence platform. If the end-user is blocked, their device is delivered a unique reference code that allows Q2 staff to decode which tool and even which-rule-on-which-tool blocked it. We can investigate – and if a false positive, we can adjust, so the tools learn and become more advanced over time. All the data and logs from these tools are pulled into a single solution, combined with application logs, and then enriched with our own risk scoring, using a criticality index and behavior anomaly detection.
We are already seeing improved results. As mentioned earlier, in 2020 Q2 blocked over 49 billion sessions from ever reaching the application layer. As proof that the cybersecurity mesh architecture is delivering results, the bad volume dropped in 2021 to nearly half – at 19 billion sessions. So far, year-to-date in 2022, we have blocked just over 7 billion while increasing users, transactions and legitimate user sessions.
At the end of the day, it’s not free for hackers to launch an attack, so if the bad actors aren’t getting a payout, they’ll move on to easier targets. Credential Stuffing has dropped by 60 percent over this period, while users have increased by 42 percent and logins have increased by 80 percent. Beyond strengthening our security posture, the integrated visibility across the attack surface allows Q2 to have much faster detection, coordinated enforcement and reduced complexity.




