Access control protection for every login, every session
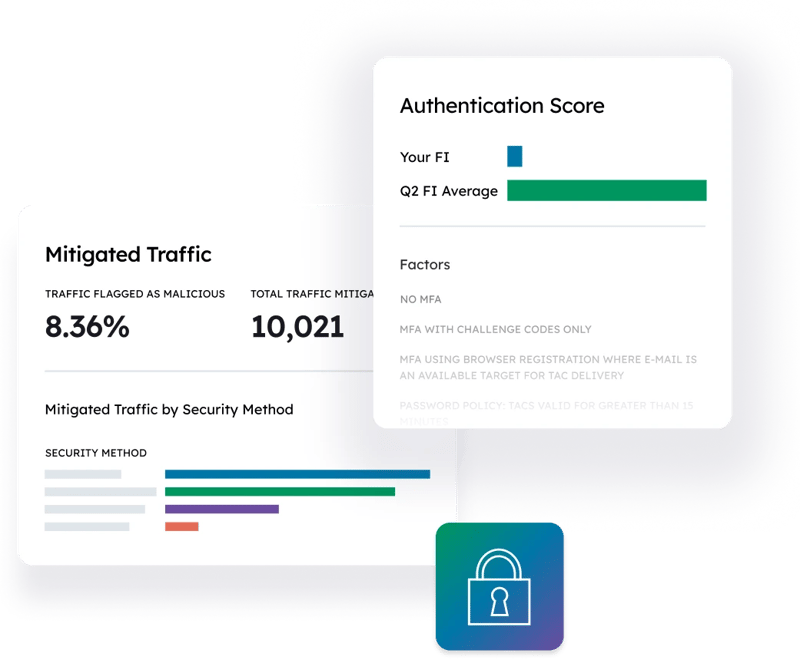
Q2 Patrol stops digital intruders before they can strike
Q2’s proven access control solutions are designed to prevent sophisticated cybercriminals from entering your digital banking environment to commit fraud or cause other havoc. Password policy management, password encryption, out of band MFA, security alerts, and biometric login options are all available—and there’s more.
For greater account holder trust and revenue generation
Knowing their accounts are safe, customers or members will be more interested in building deeper relationships with your FI.
Gain a competitive differentiator
Having a more complete access control framework will gain more account holders—they’ll appreciate your embrace of innovation to stay ahead of cybercrime.
Meet compliance
Ensure legal and policy requirements and governance while making reporting and auditing processes more efficient.
Zero Trust is in place to put a stop to intrusions
Zero Trust principles are at work at Q2 to bring more complete security to FIs and account holders. Our distributed cloud approach is protected by a Secure Access Service Edge (SASE), giving Q2’s Integrated Operations Center (IOC) constant threat visibility and mitigation for your FI and account holders.
Q2 continuously verifies a user’s rights
Constant authentication and authorization access to your FI’s systems and network.
Least-privileged policies are in place
Limit user access with just-in-time and just-enough access.
Breaches are prevented
Q2 segments access by network, user, device, and application awareness to avoid breaches.
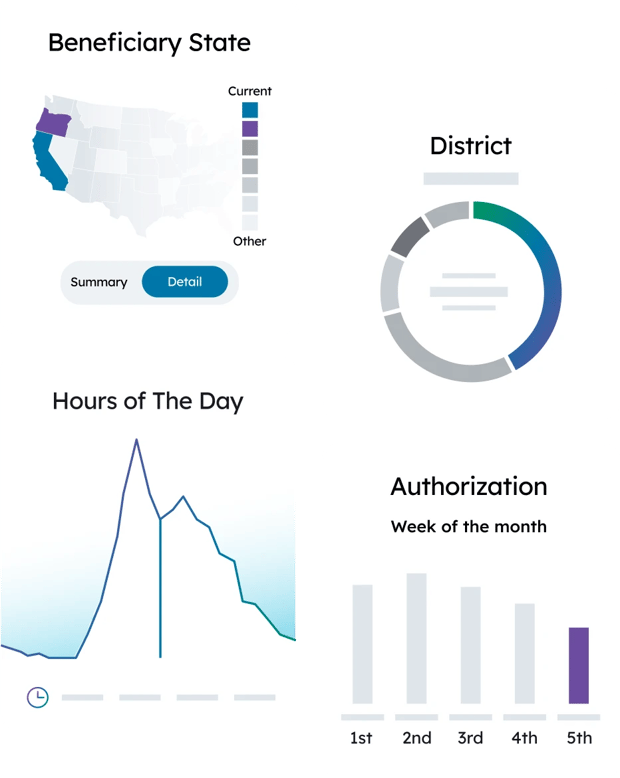
Access monitoring with anomaly detection
Monitoring login and behavior patterns with Q2 Patrol™ allows us to optionally prompt users for step-up authentication before accessing high-risk events when we detect anomalous activity. Access details are continuously tracked—including day and time, state location of IP address, device type (mobile, tablet, desktop), and browser/app—and anomalies found in use patterns trigger Q2 Patrol™.
Authentication can occur via Secure Access Code (SAC) or Symantec token (virtual or physical).
Add users, change alerts, authorize external transfer, and change contact information when needed
Your FI also can access administrative reporting of user logins and device details for reviews.
Blockchain keeps critical data safe
Obtain tamper-proof storage that is invulnerable to bad actors, even at the “last mile” that connects applications to data. The blockchain technology of Q2 TrustView safeguards critical data by fragmenting personally identifiable information across a private, low latency blockchain network. This layer of access control is designed to complement our security solutions, while simultaneously focusing on adherence to privacy regulations domestically and worldwide.
Leverage the append-only architecture inherent in blockchain technology
Utilize a comprehensive, immutable view of authorized users accessing valuable data, when they access it, and how often to better control the inner data environment.
Even more protection layers
Based on your customer composition and level of global commerce, you can enable extra protection layers to prevent additional undesirable logins with our OFAC login restriction service. This service can be configured to restrict direct access from countries that are listed for U.S. Treasury sanctions, or a higher tier which includes additional high-risk countries.
With Q2 Security Insights, your FI can get deeper visibility into the full set of network traffic managed by Q2 to correlate signals from your Q2 stack for your own security assessment purposes.

-
“CISOs are increasingly acknowledging that it will require more than just raising employee security awareness, if the objective is minimizing cybersecurity risk exposure from eminently avoidable employee actions. Enterprises that are serious about human risk management must go further.”
GartnerRead story
4 Ways to Achieve Secure Employees, 2023 -
“Remember that the efficacy of zero trust depends on 100% deployment. That means everyone uses multifactor, every bit of data is protected, and every endpoint has anomaly detection. Vulnerability at a single access point can create vulnerability in the entire system.”
Lou SenkoRead story
Chief Availability Officer, Q2
How does access control work in banking?
Access control helps financial institutions restrict and manage access to their digital banking environments, to protect account holders. There are a variety of ways access control can be maintained, including multifactor authentication, password encryption, security alerts, and biometric login options.
What is zero trust security?
When a financial institution implements a zero trust security framework, they are assuming that no user should be trusted without first requiring them to go through a verification and authorization process each time they request access to sensitive financial information.
Resources
Additional products
-
Behavioral Analytics and Fraud Prevention
Prevent fraud before it happens.
-
Positive Pay
Put superior check and ACH fraud prevention to work.
-
ACH Processing & Reporting
Better meet compliance requirements.